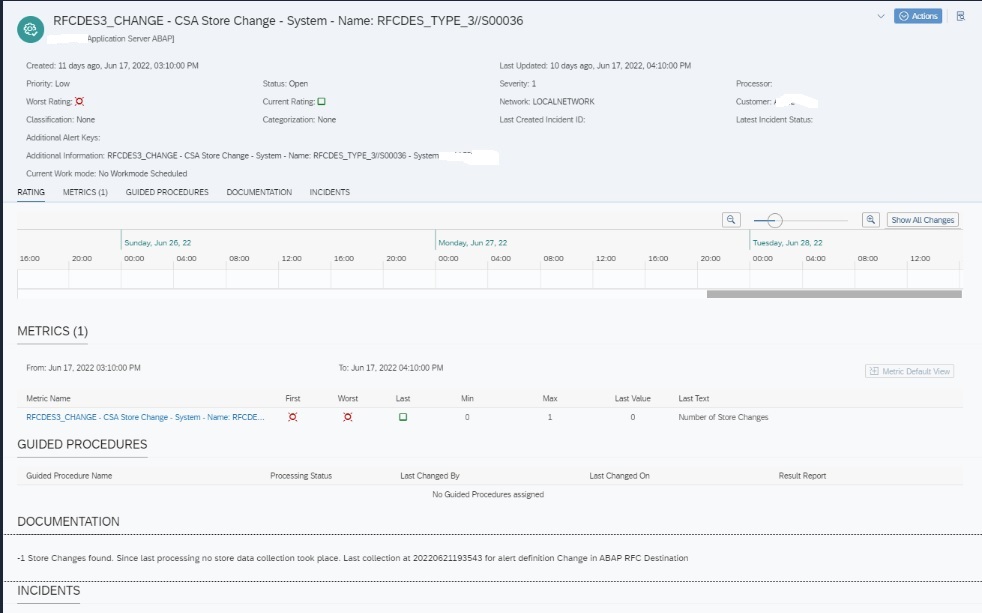
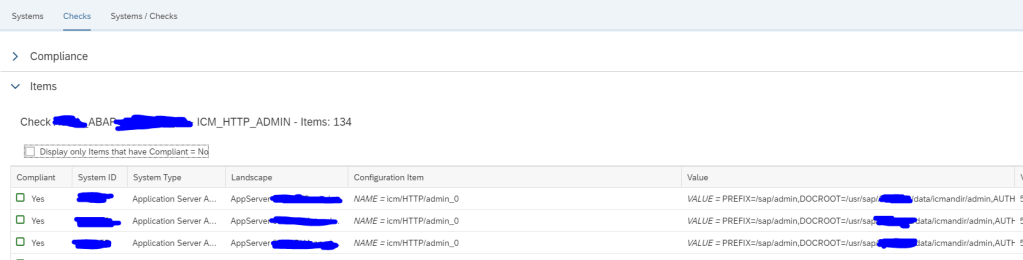
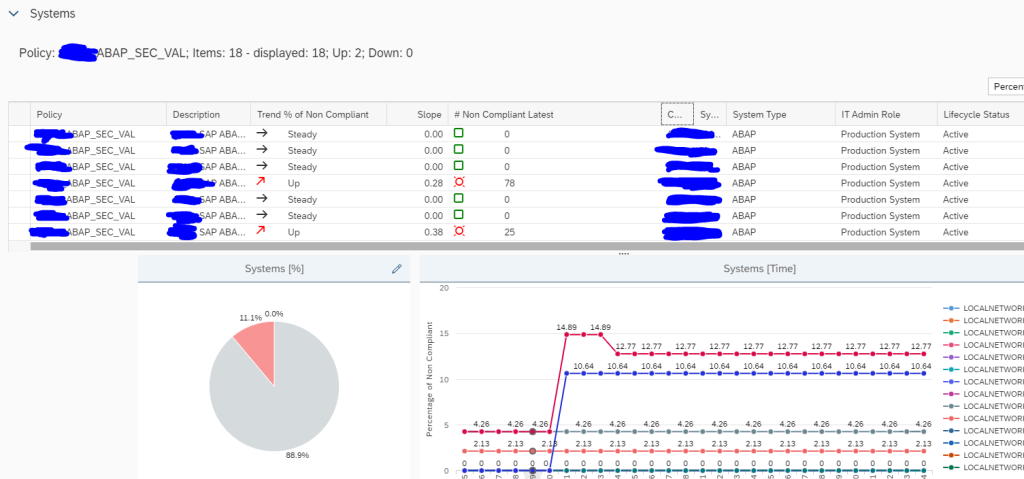
SNC Certificate expiry is very critical for ABAP systems where SNC logon is used. As soon as the certificate expires users will no more be able to login to system.
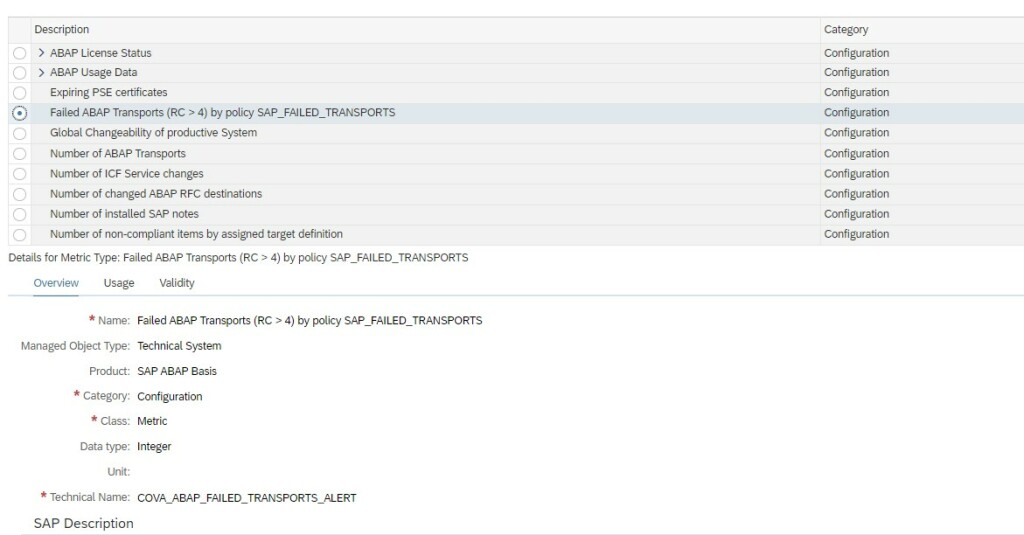
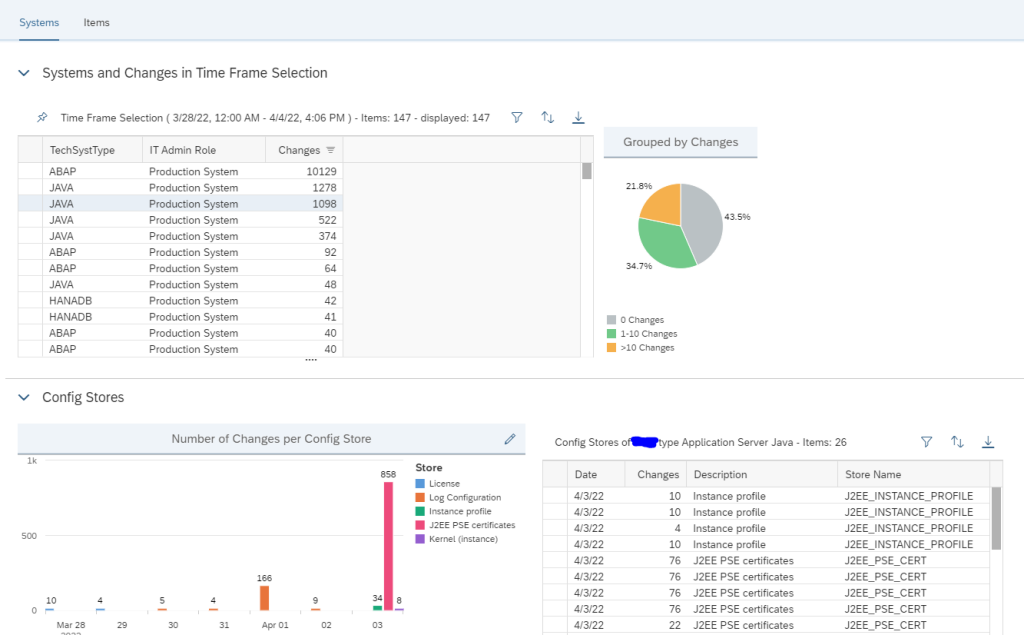
In System Monitoring for ABAP systems SAP provides a standard metric called Expiring PSE Certificates which monitors all PSE certificates that includes SNC certificates. When this metric turns red it will tell how many certificates are expiring/expired but not which one. Hence its beneficial to monitor separately the status of SNC Certificates.
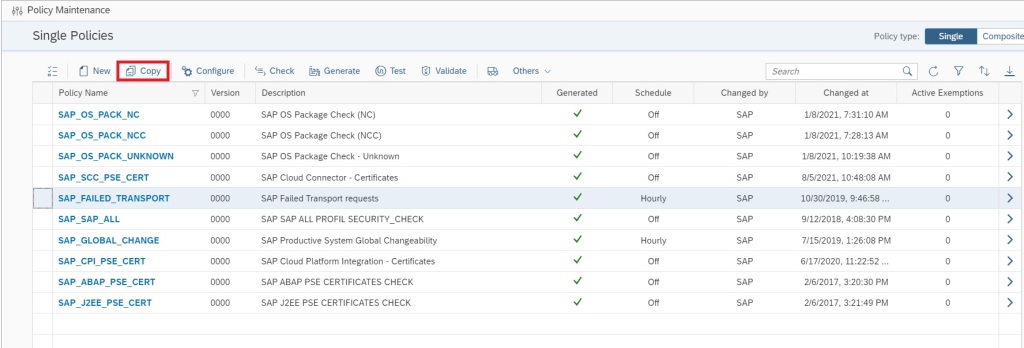
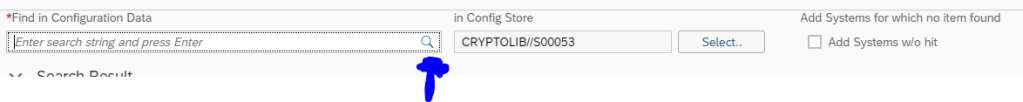
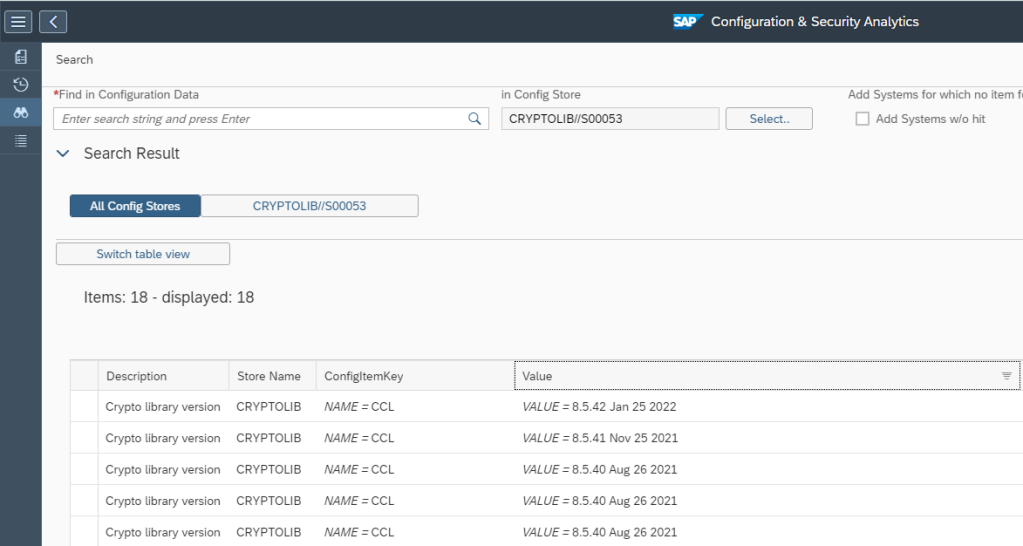
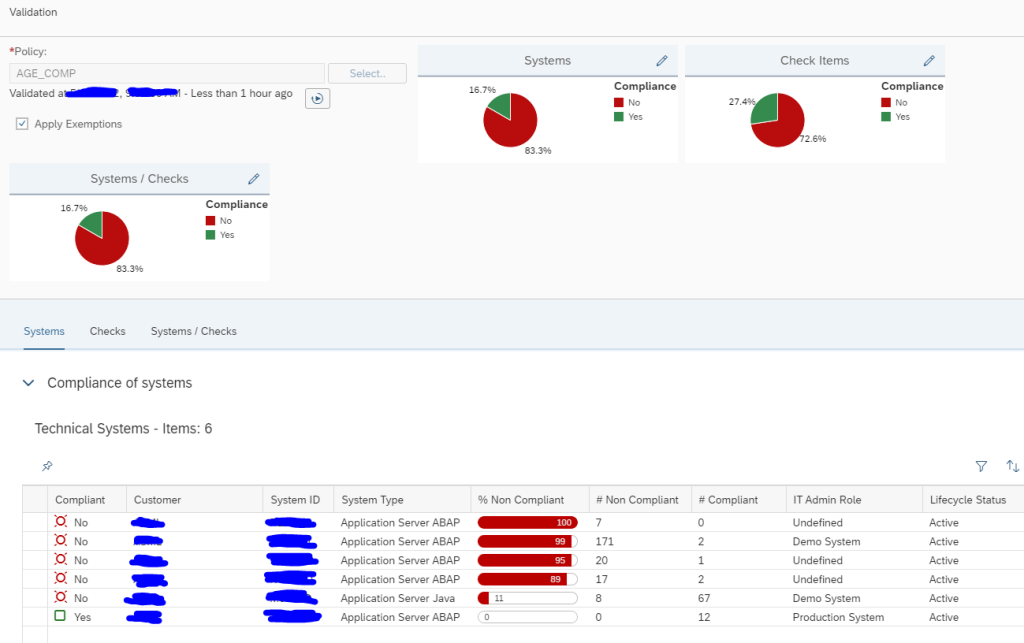
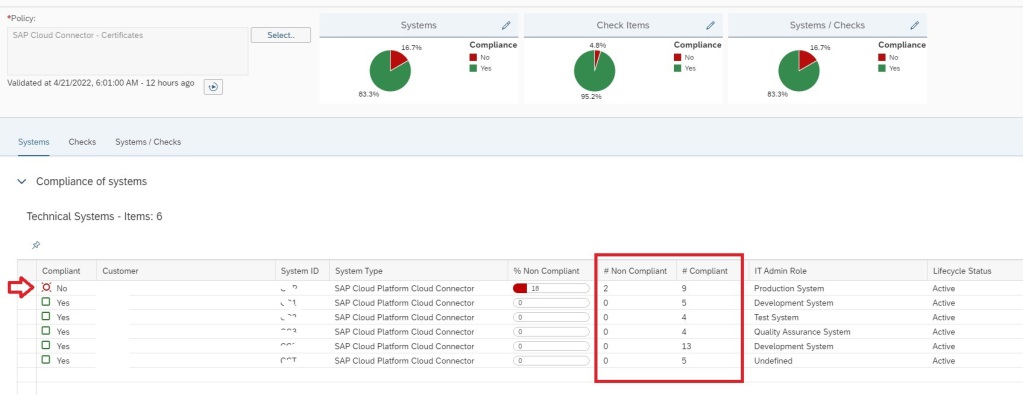
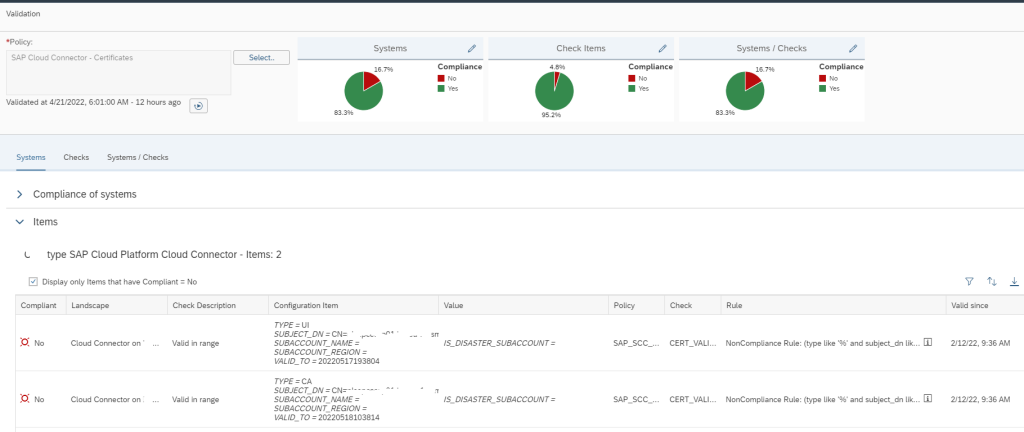
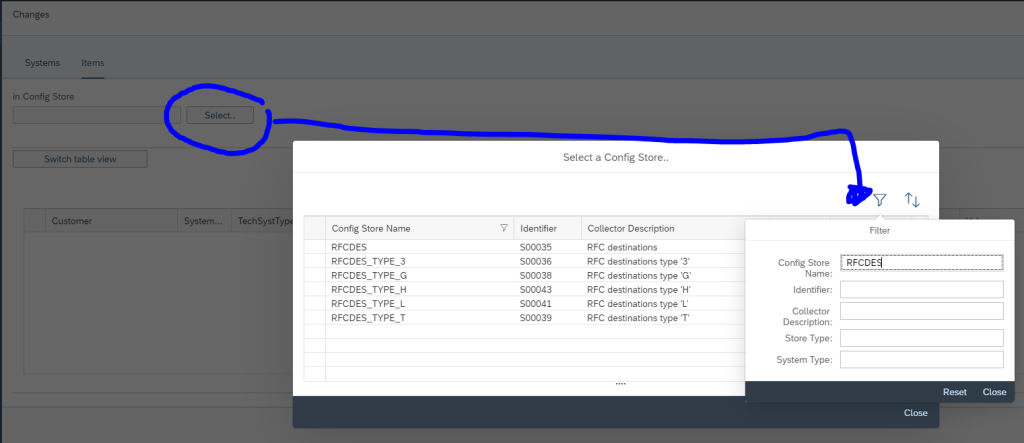
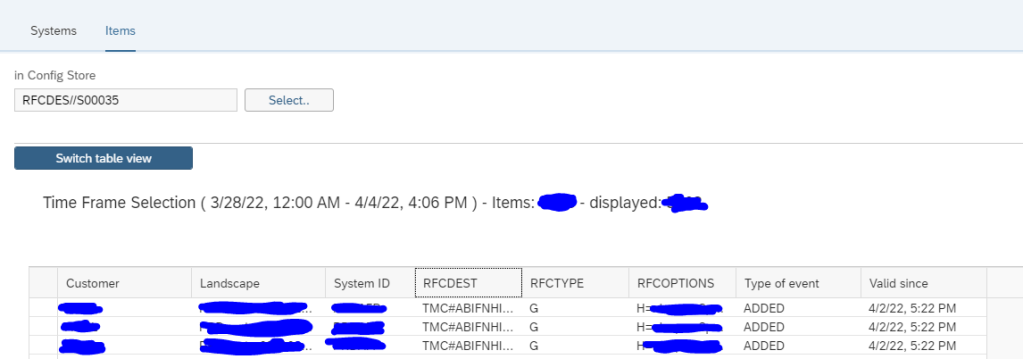
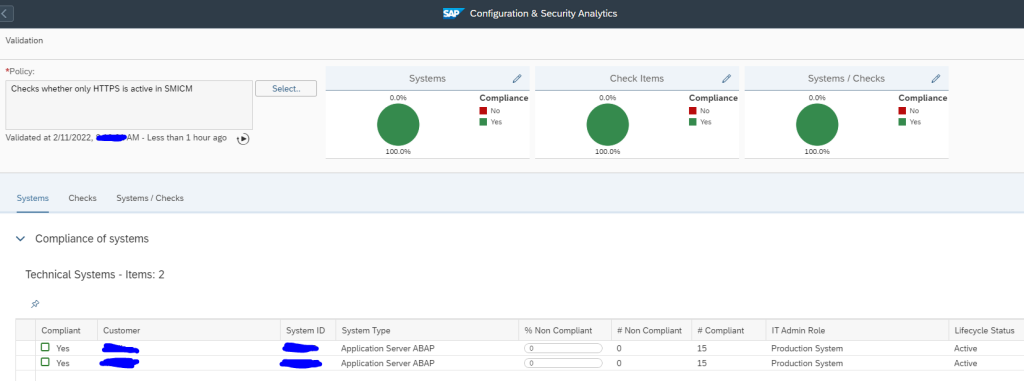
This monitoring can be achieved by using Config Validation.
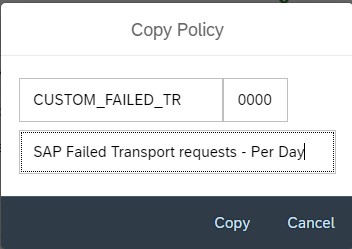
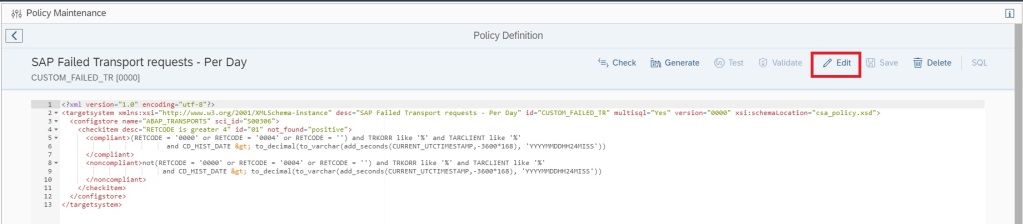
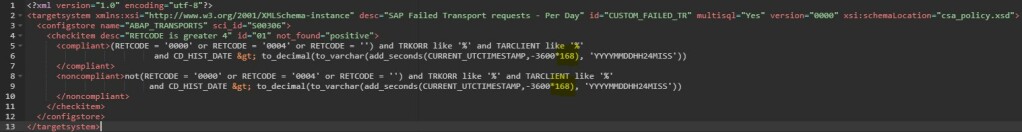
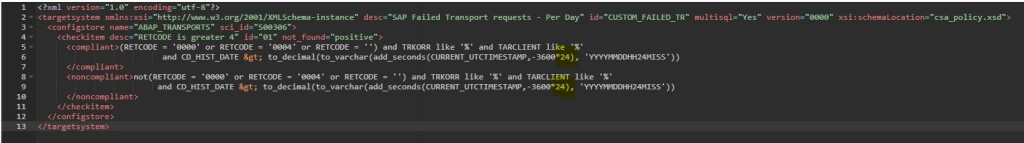
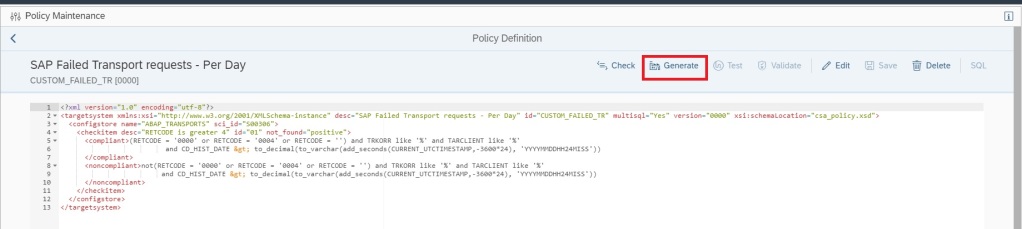
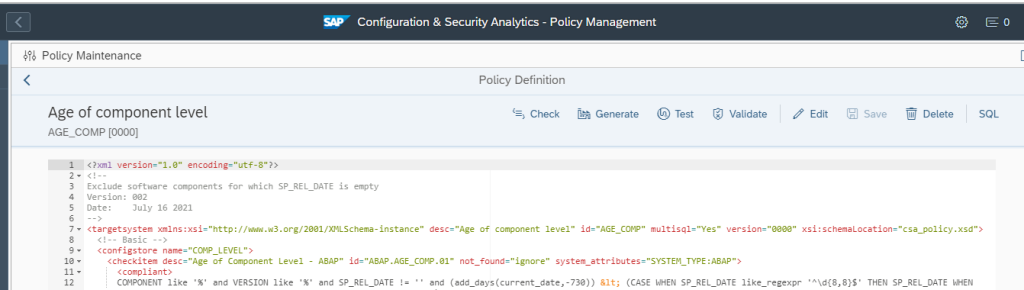
You can create a custom policy with the below XML code that checks the PSE_CERT store to check on status of SNC Certificate.
<?xml version="1.0" encoding="utf-8"?>
<targetsystem desc="SNC Certificate about to expire" id="ASML_SNCERT_TOBE_EXP" multisql="Yes" version="0000">
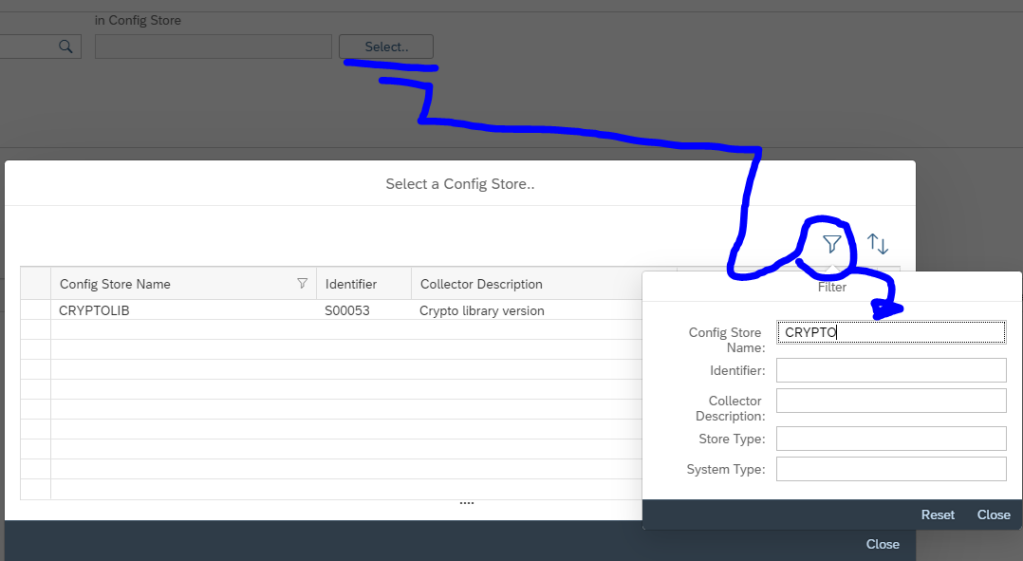
<configstore name="PSE_CERT" system_type="ABAP">
<checkitem desc="Valid in range" id="1" operator="">
<compliant>APPLICATION like '%SNCS%' and CONTEXT like '%' and TYPE like '%' and SUBJECT like '%sapci%' and ISSUER like '%' and SERIALNO like '%' and VALID_FROM like '%' and ( ( ( replace_regexpr ('^$' IN valid_to WITH (replace(current_date, '-', '')||replace(current_time, ':', '')))) > to_number(replace(add_days(current_date, 30), '-', '')||replace(current_time, ':', '') ))
or (( replace_regexpr ('^$' IN valid_to WITH (replace(current_date, '-', '')||replace(current_time, ':', '')))) < to_number(replace(add_days(current_date, 0), '-', '')||replace(current_time, ':', '') )) )</compliant>
<noncompliant>APPLICATION like '%SNCS%' and CONTEXT like '%' and TYPE like '%' and SUBJECT like '%sapci%' and ISSUER like '%' and SERIALNO like '%' and VALID_FROM like '%' and not ( ( ( replace_regexpr ('^$' IN valid_to WITH (replace(current_date, '-', '')||replace(current_time, ':', '')))) > to_number(replace(add_days(current_date, 30), '-', '')||replace(current_time, ':', '') ))
or (( replace_regexpr ('^$' IN valid_to WITH (replace(current_date, '-', '')||replace(current_time, ':', '')))) < to_number(replace(add_days(current_date, 0), '-', '')||replace(current_time, ':', '') )) )</noncompliant>
</checkitem>
</configstore>
</targetsystem>Note: In the above XML code, SUBJECT like ‘%sapci%’, you have to replace sapci with a hostname pattern that you use for all your SAP ABAP system hostnames.
To know more about policy maintenance you can refer to our below blog where in we have explained in detail with another example how to maintain policies, edit the XML code and then generate the policy.
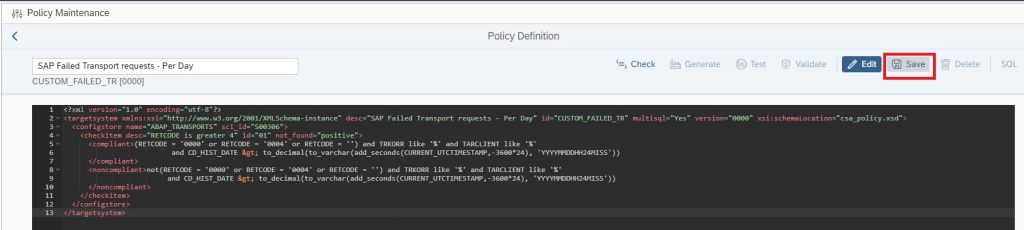
Once you have created the policy, you can directly activate alerting on the policy.
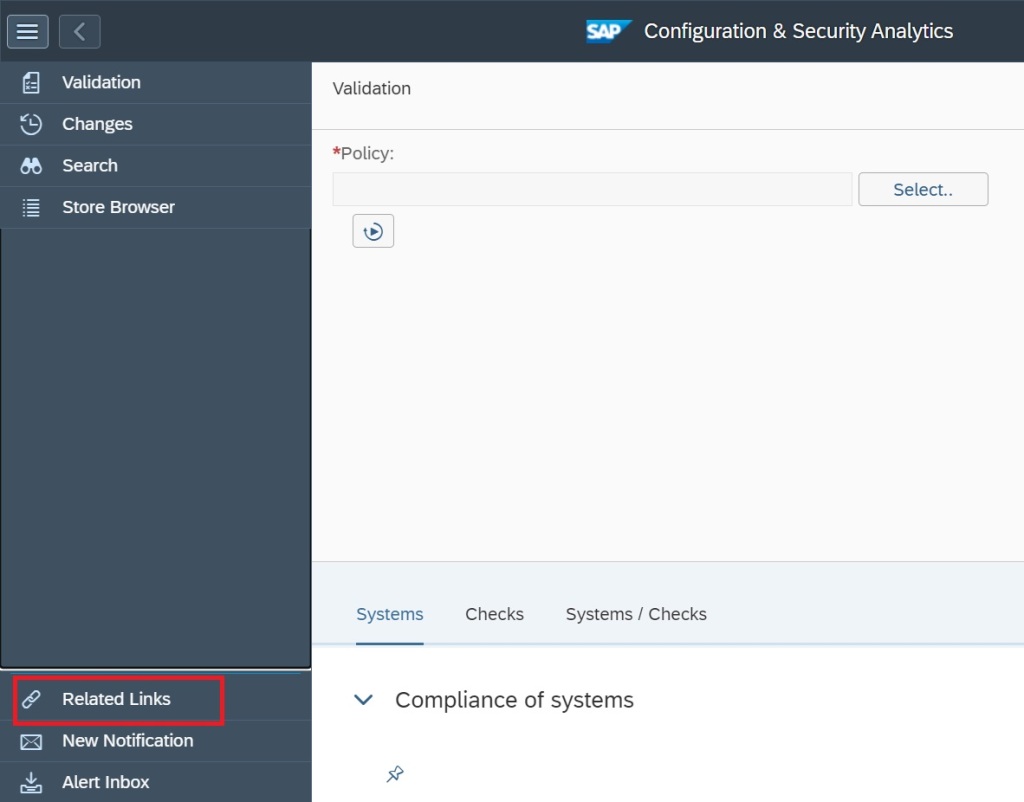
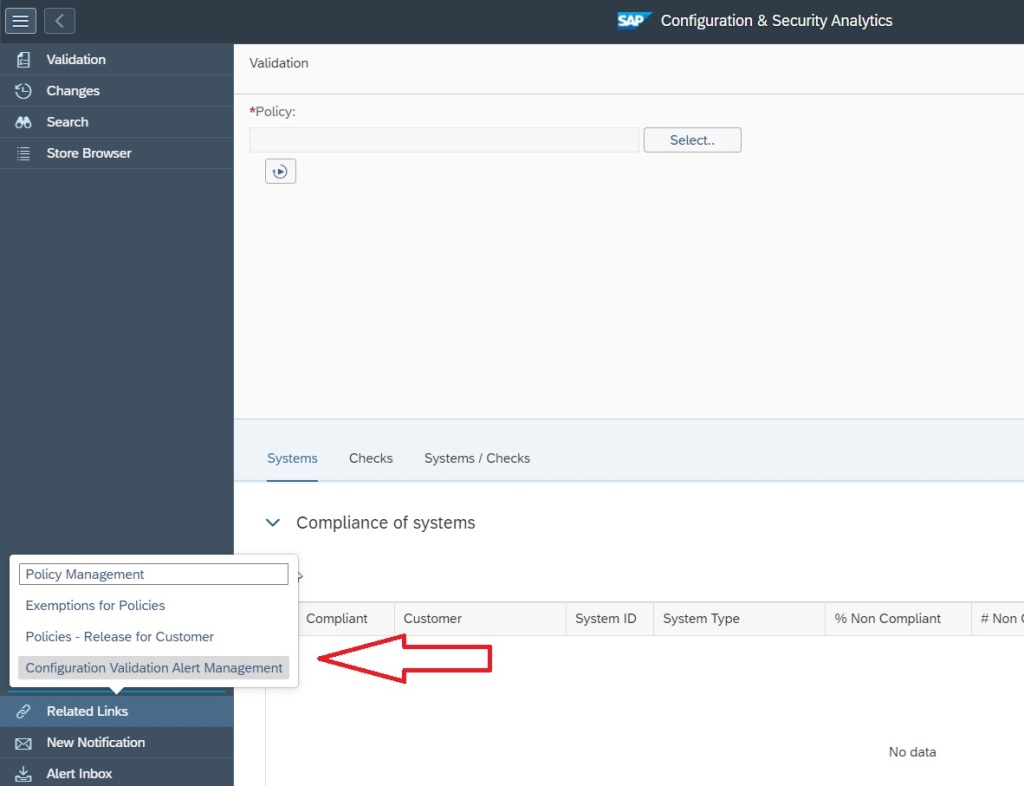
For that go to the Configuration and Security Analytics app in the Advanced Configuration Monitoring area.

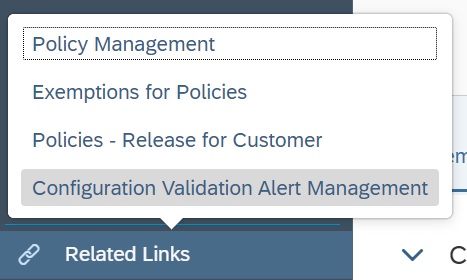
In the app navigate to Configuration Validation Alert Management under the the Related links tab.
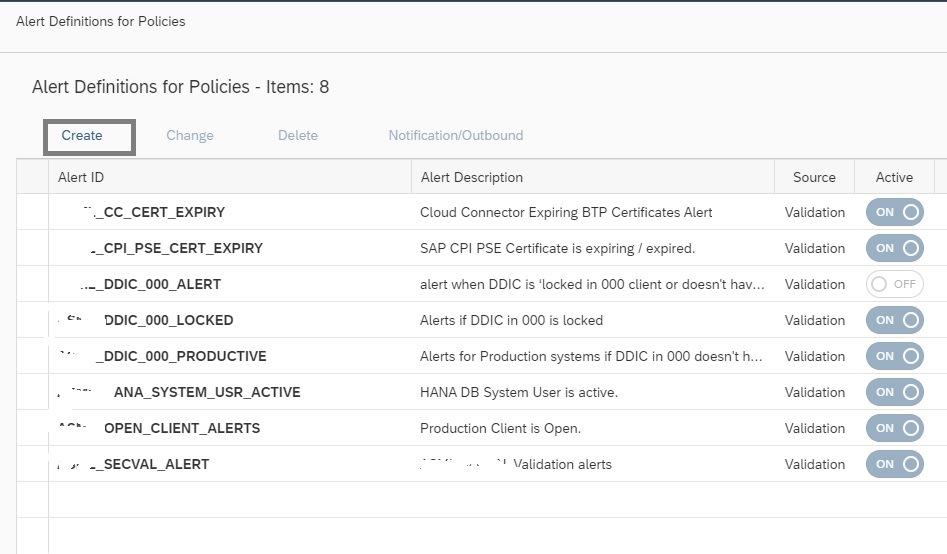
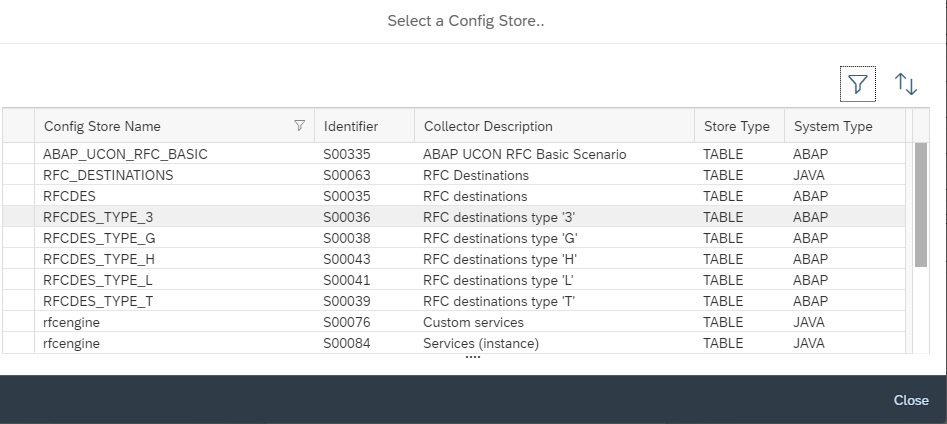
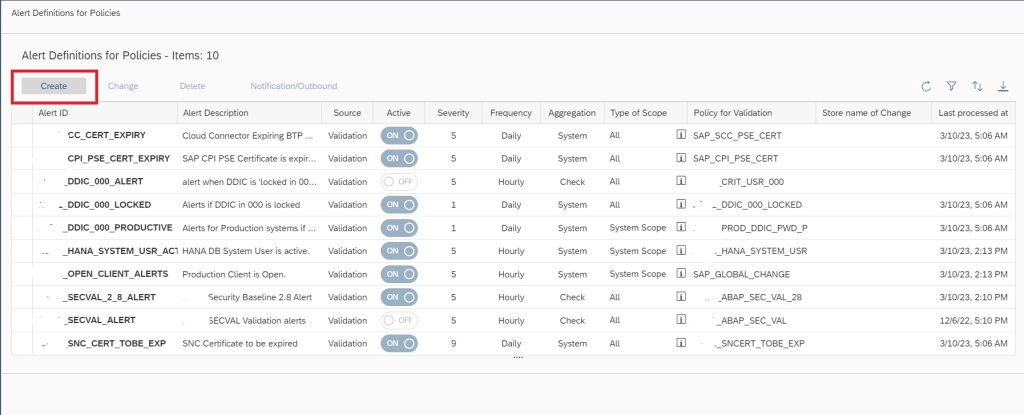
In the Alert Management app click on Create button to create the alerting for the policy you just created.
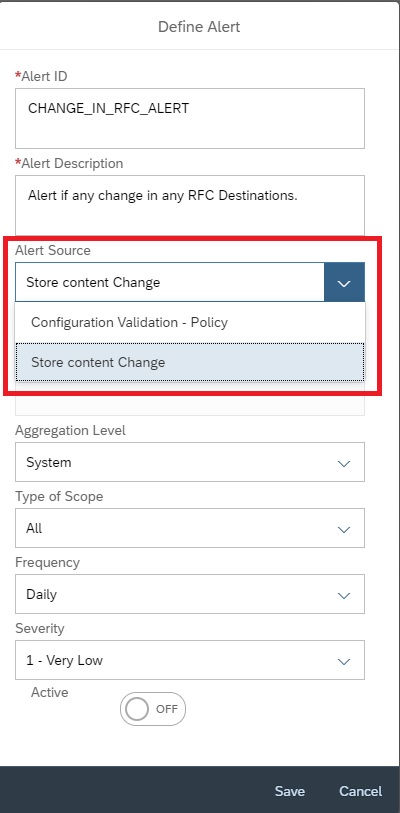
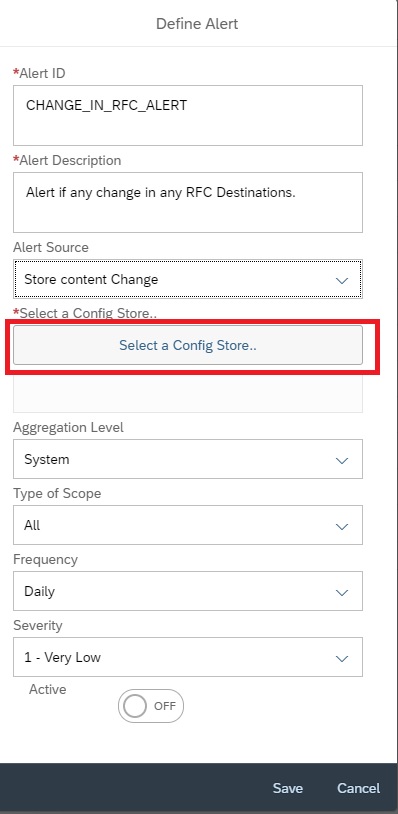
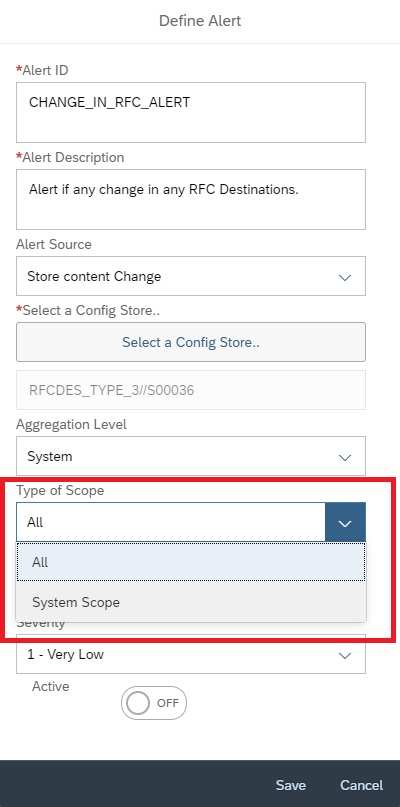
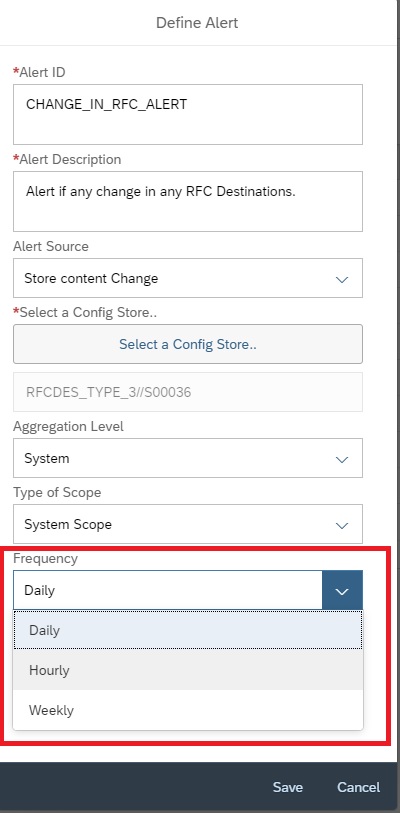
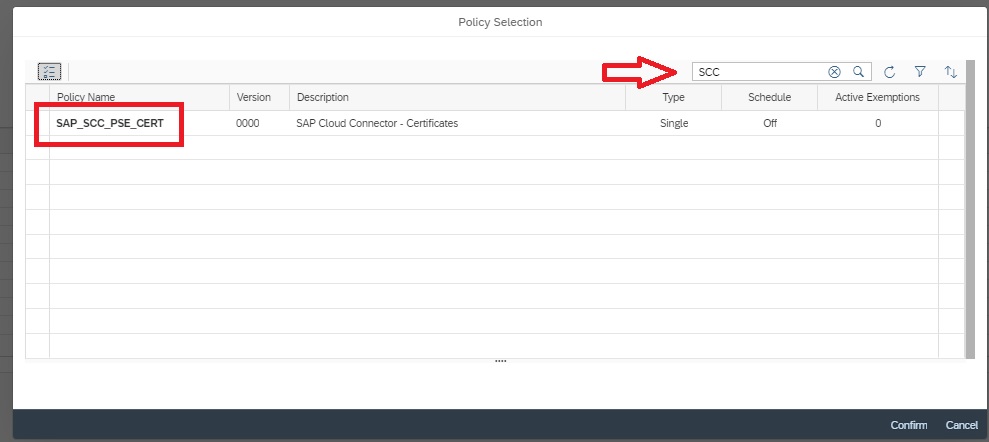
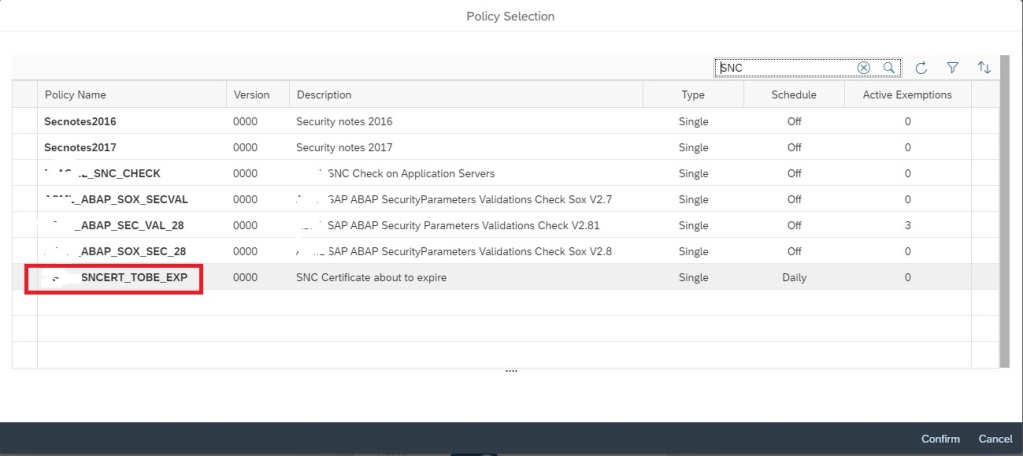
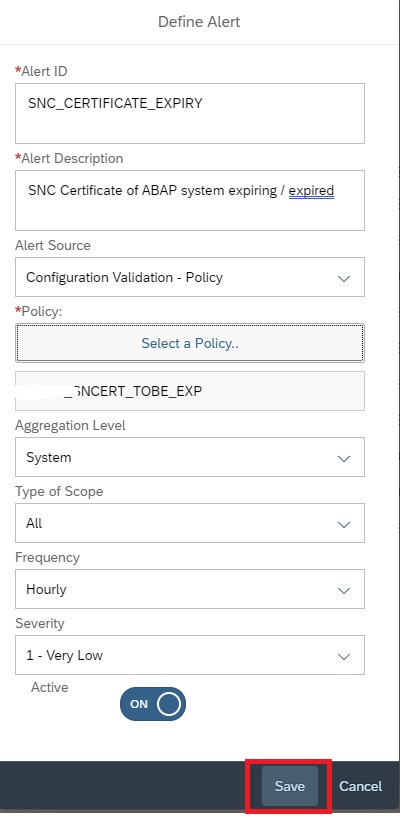
In the next popup, enter details as shown below and then click on Select policy to select the policy for which you want to activate the alert.

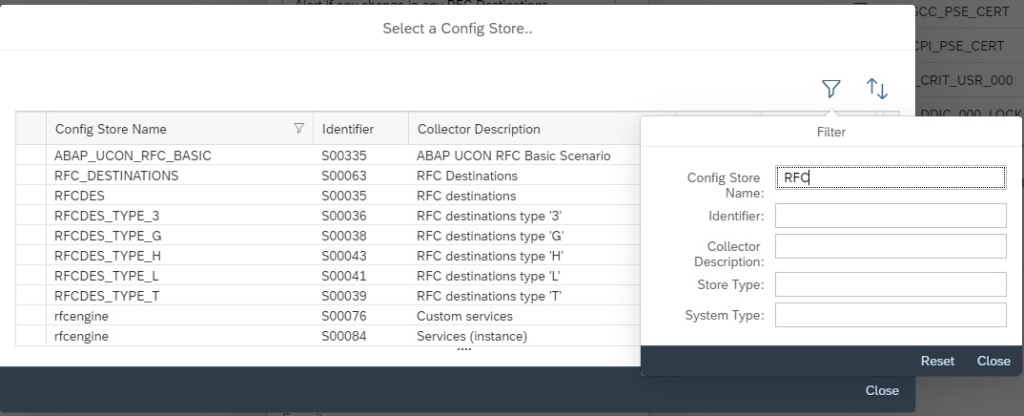
In the next popup select the policy by clicking on the policy name.
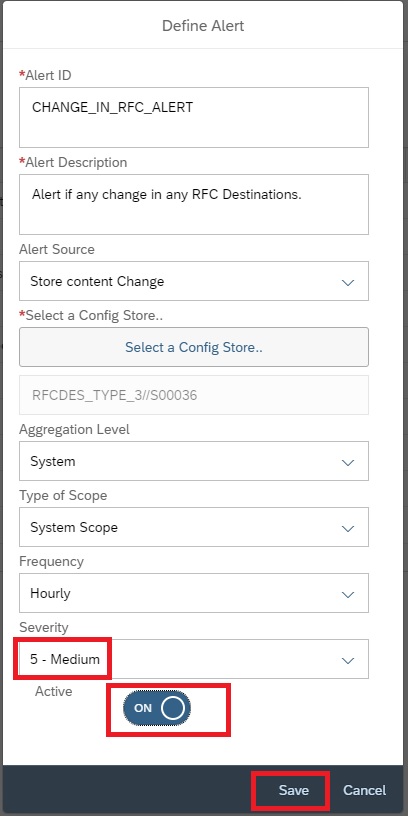
Now click on Save to activate the alerting.
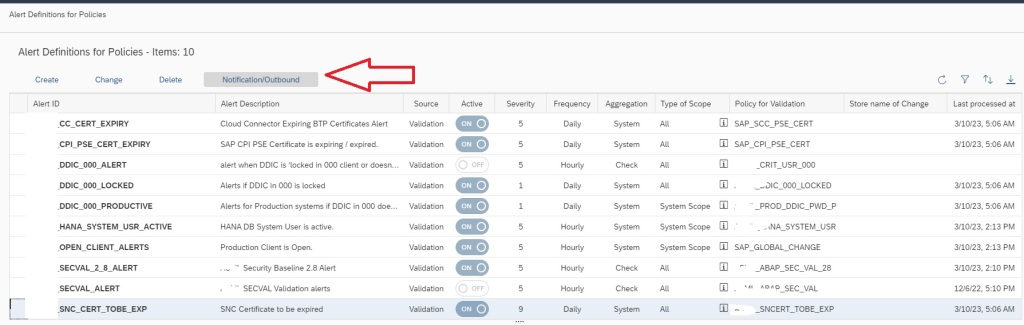
Additionally you can also activate email notification on the alert. For this in the Alert Management main screen, select the alert and then click on Notification/Outbound
In the next popup select the notification variant and save.

Now your alerting is active along with notification for SNC certificate expiry.
For more details on Config Validation you can refer to SAP documentation here.