For an SAP Application Management team in any IT landscape , doing a timewise tracking of transport movement across SAP System Landscapes is a very important monitoring requirement.
In this blog I’ll explain how you can do transport tracking, using Configuration Validation Trend Analysis application. With this you can track how many transports got imported verses how many got failed.
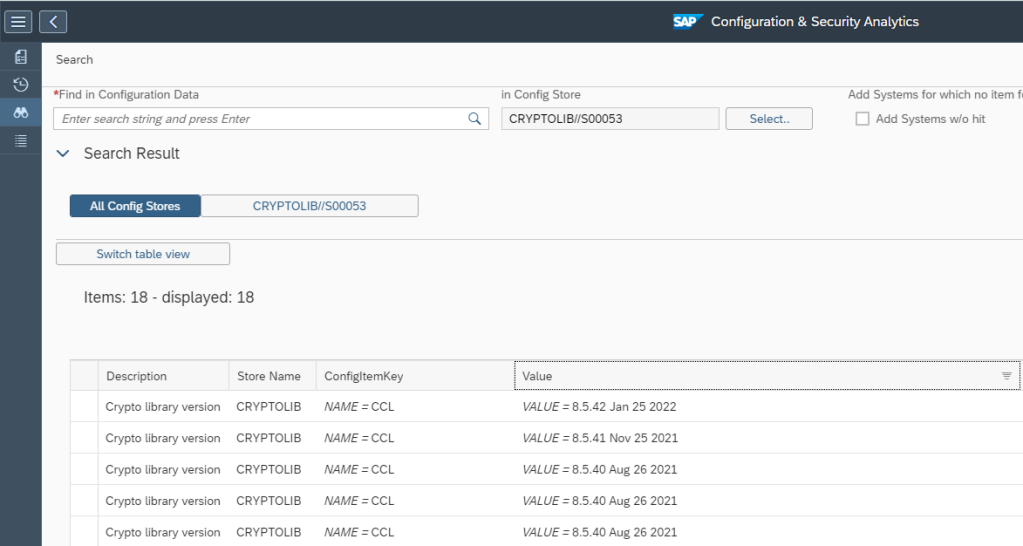
SAP provides a standard configuration validation policy called SAP_FAILED_TRANSPOTS that collects last 7 days data from config store ABAP_TRANSPORTS of SAP ABAP managed systems. SAP uses this policy result for the system monitoring metric for failed transport.
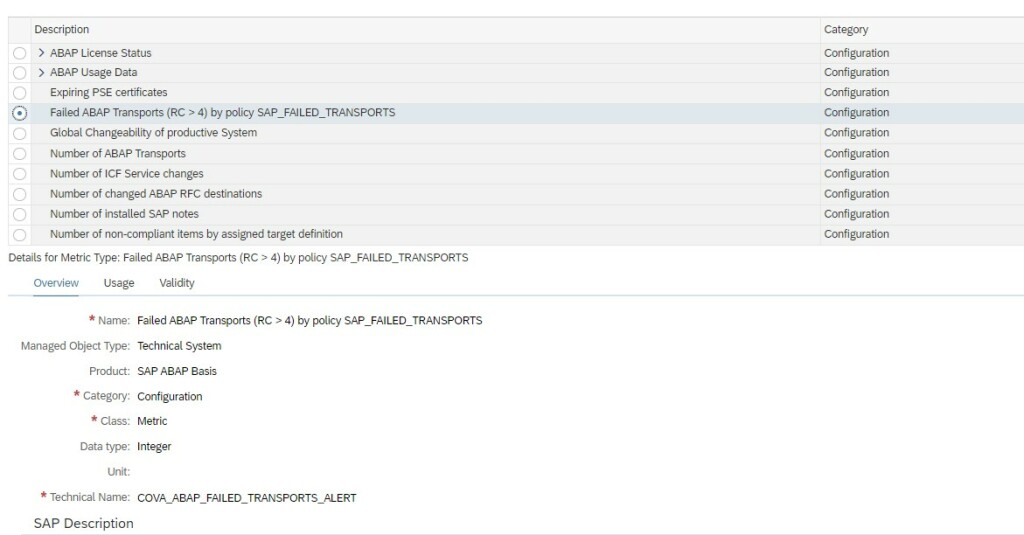
To be able to see a day wise trend for transports you will have to first copy this standard policy to a custom policy and change the time period of compliance rule in the policy from last seven days to last 1 day.
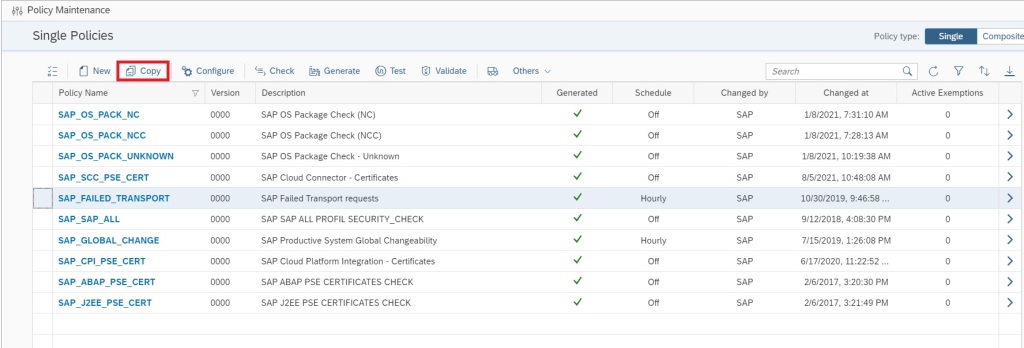
For this first you navigate to Policy Management app in Advanced Configuration Monitoring area in SAP Focused Run Launchpad.

In the Policy Management App select the policy SAP_FAILED_TRANSPORTS and copy.
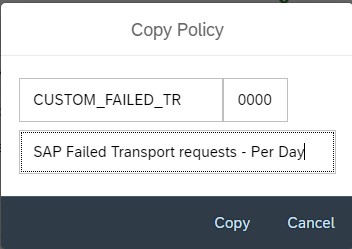
Provide a custom policy name and description and copy.
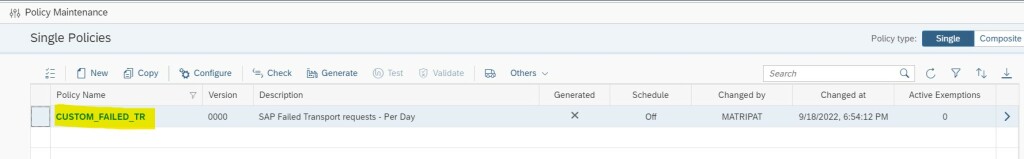
Now you will be back in the main screen, click on the custom policy name you just created.
In the policy editor screen click on Edit button to start editing your policy.
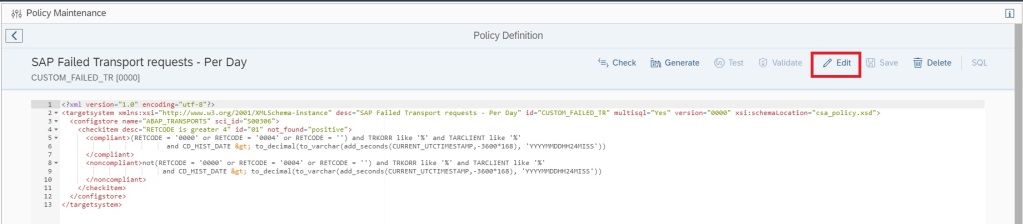
In the compliance rule change the hour value in CURRENT_UTCTIMESTAMP,-3600*168 from 168 to 24 CURRENT_UTCTIMESTAMP,-3600*24
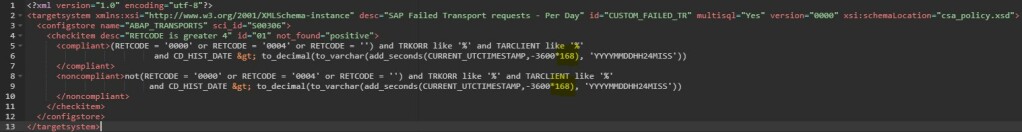
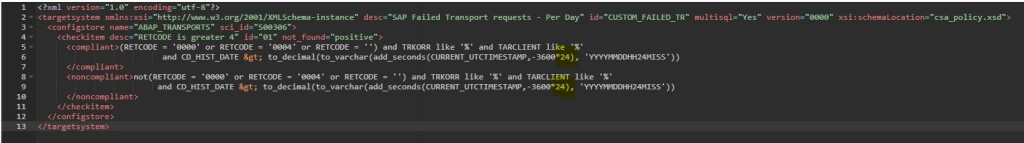
Save the policy by clicking on Save button.
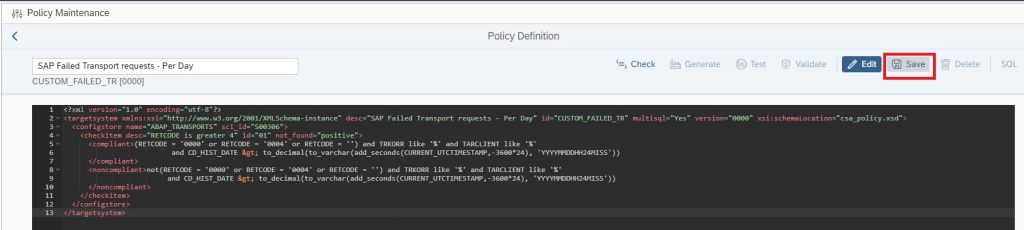
Now generate the policy by clicking on Generate button.
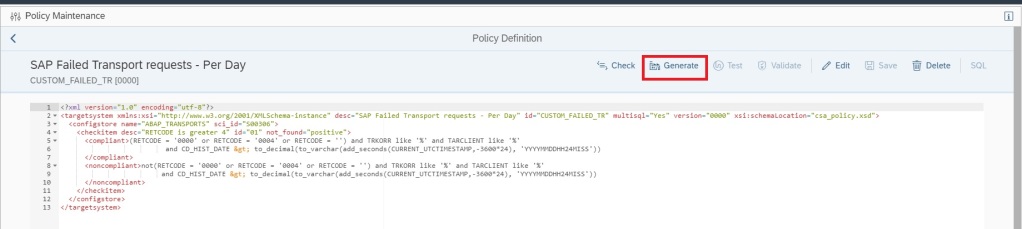
Now you can validate if the policy is working fine by clicking on the Validate button.
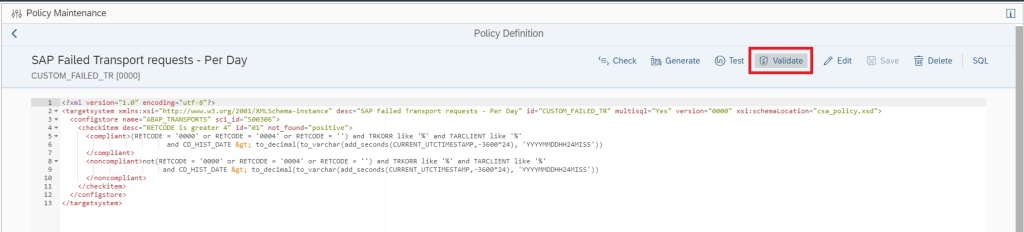
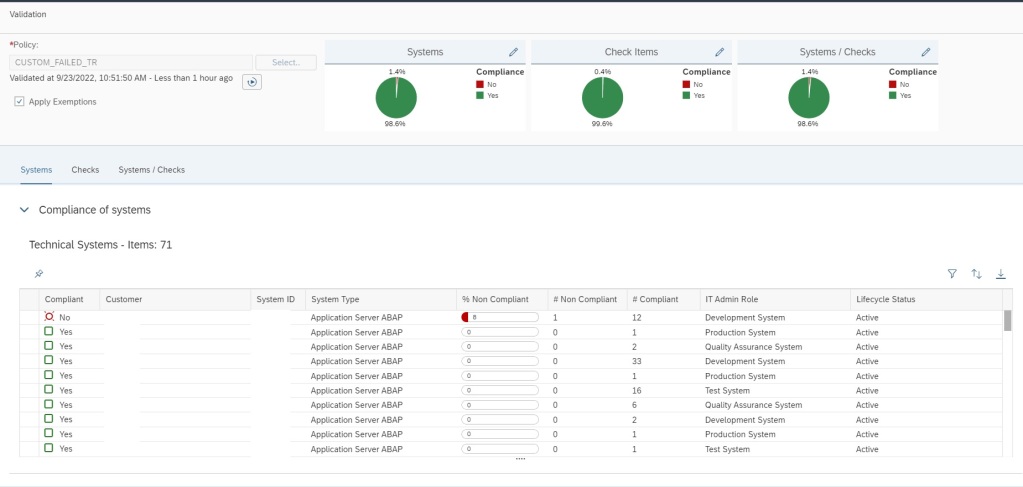
If no error is there, in a new window you will see the validation results as shown below.
Now your custom policy is ready, but before you can use this policy for Trend Analysis you need to activate periodic data collection for this policy. For this navigate back to the main screen of Policy Management app.
In the main screen select the custom policy and click on Configure.
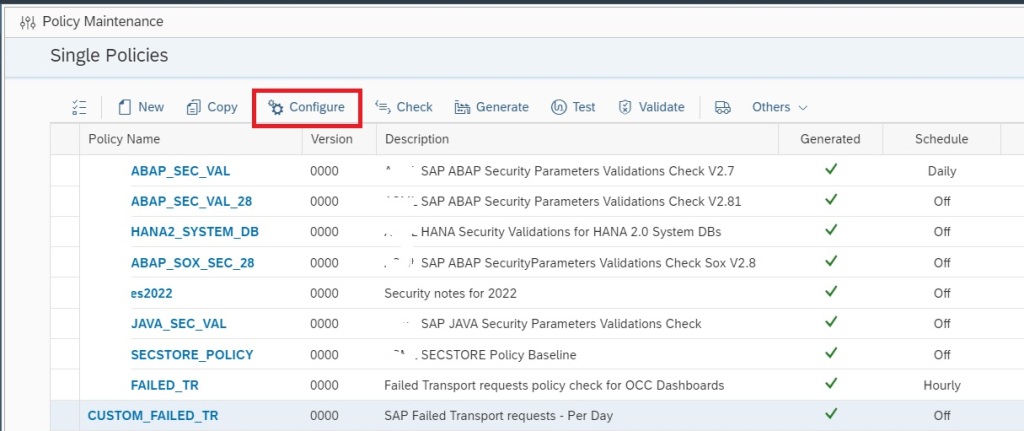
In the next pop-up window click on Edit button to continue.

You can now set the Validation run interval to Hourly or Daily and then save and exit.
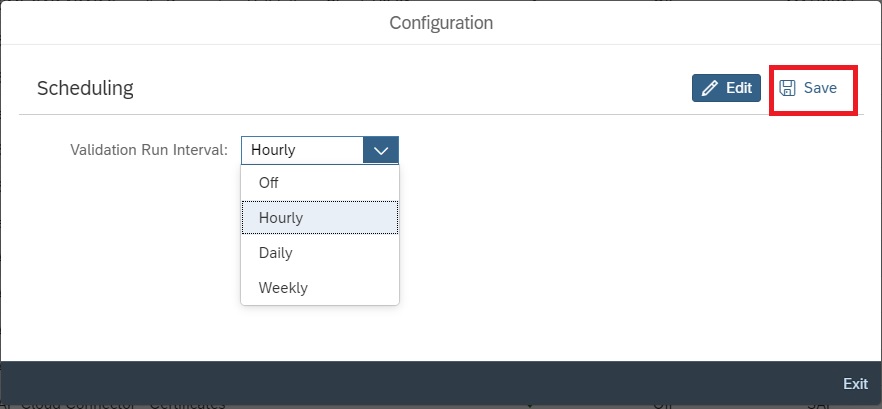
After you schedule the validation wait for at least one week to see the data in the trend analysis app. Data will be available only from the time you activated the validation run schedule.
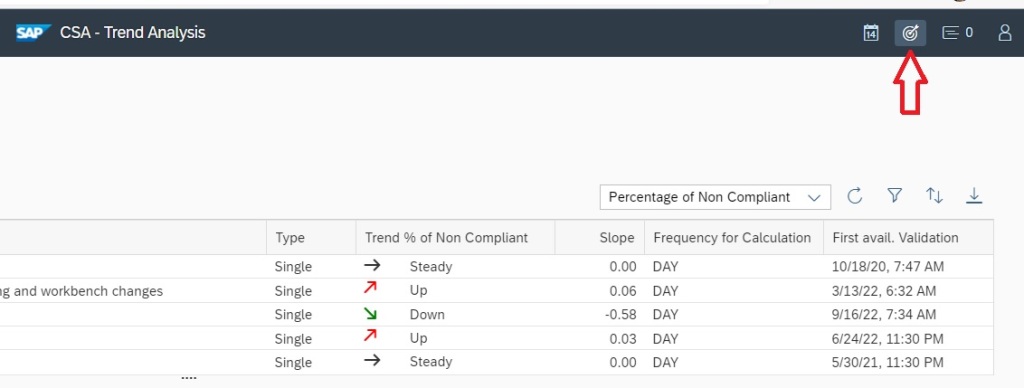
Now you can run Trend Analysis on this custom policy to do transport tracking. For this navigate to the Configuration & Security Analytics Trend Analysis App in the Advanced Configuration Monitoring area of Focused Run launchpad.

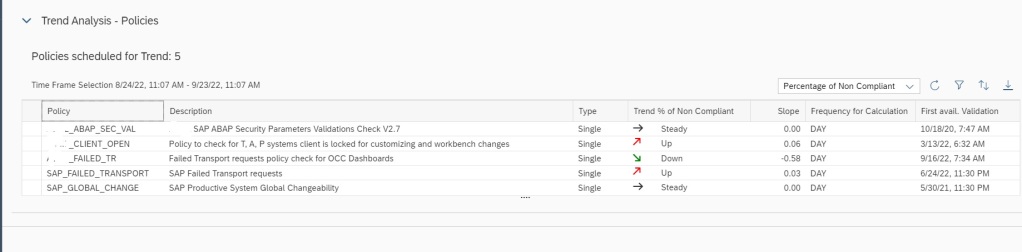
In the home screen app you will see the trend overview of the policies which are scheduled for validation run and for which data is available.
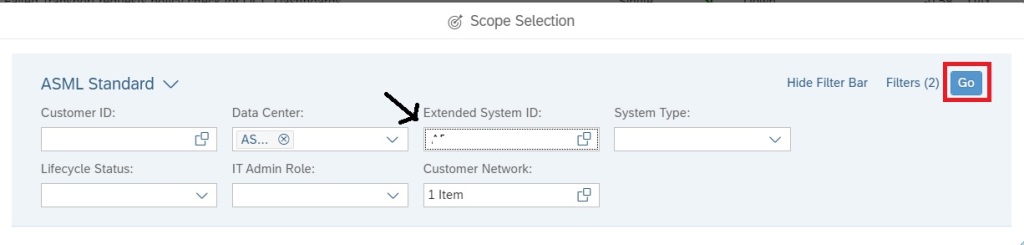
To do transport tracking on the custom policy you created and scheduled for validation, first select the managed system for which you want to do tracking in the scope selection.
After selecting scope, select the policy and in the the Key Figure dropdown select All items to see Number of transports imported to the managed system. If you select key figure Non Compliant it will show you the numbers for failed imports.
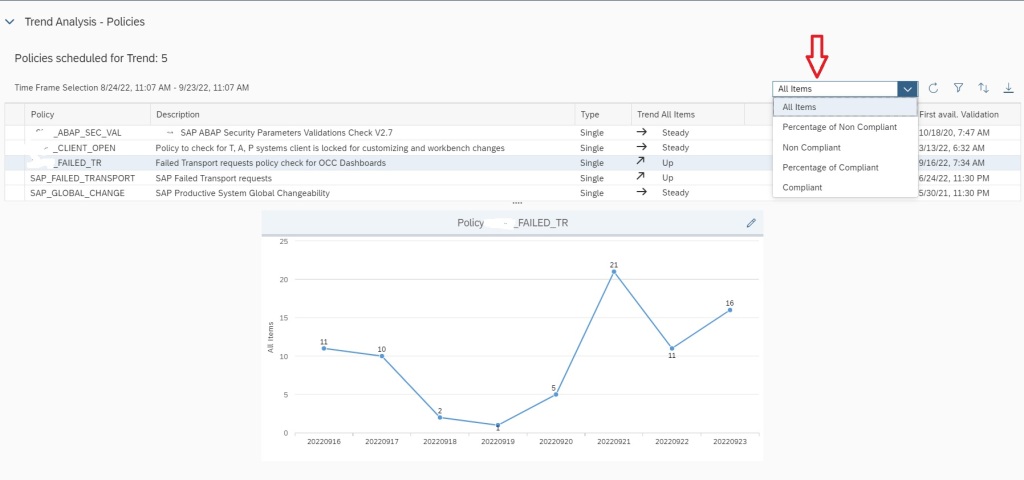
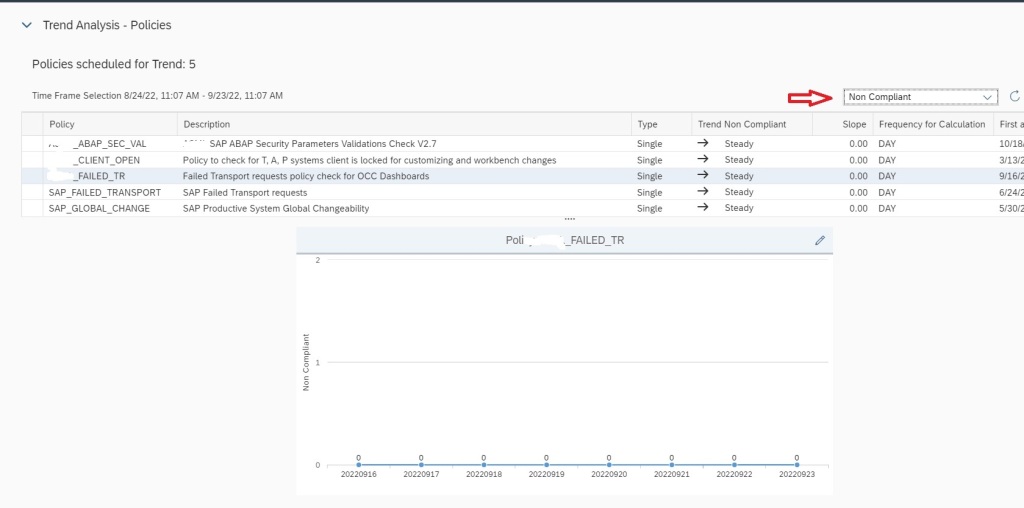
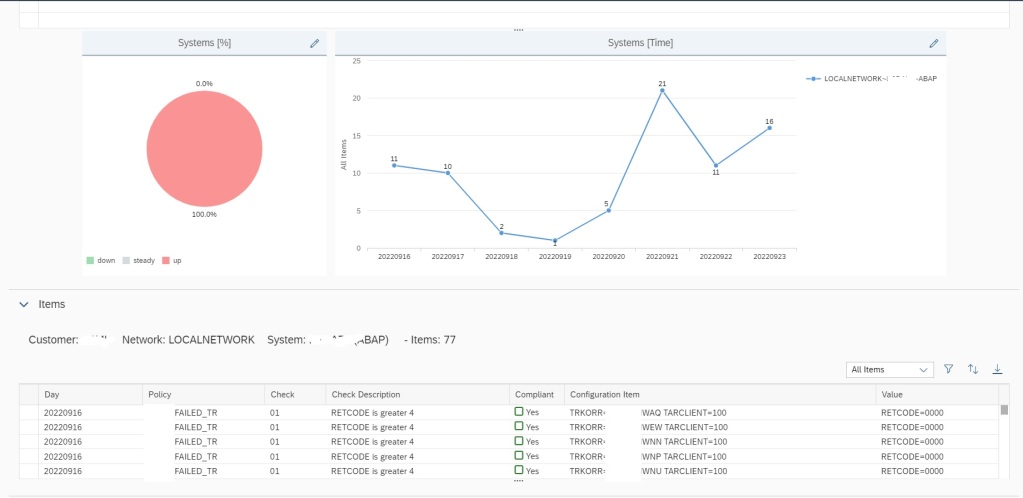
If you scroll down, you can also find details of each transport that were imported in the managed system in the specific time frame shown in the graph.
To know more possibilities with SAP Focused Run Configuration and Security Monitoring you can refer to our blogs here.
You can also find SAP manuals on Configuration and Security monitoring here.